Serena by Ron Rash
While it may sound harsh, I think this is probably a better movie than book. The story was not terrible but the characters were lacking in any real dimension. The attributes of the title character (and I am being circumspect to avoid spoilers) were never fully explained and while not unbelievable just left you thinking of her more as a caricature than a character of depth and substance.
Good for a read if you don’t want to think too much about the story. Very much Dan Brown territory
Firstly I need to say that Peripheral: Tales of Horror at a Glance isn’t a horror novel at all. It contains drama and suspense but not horror. Think more Twilight Zone rather than Stephen King and you will have a better idea of the style of the book.
Overall I quite liked this novel. The different stories were engaging and interesting. Some I found better than others of course but that is often the case with collection of short stories I find. There is a connective thread through a number of the different stories which I found intriguing and something that kept you going through the book.
Looking forward to more works by Sylvester Pilgrim
There has been some growing speculation as to whether the NSA was aware of the Heartbleed vulnerability in advance. The story was raised and reported by Bloomberg, denied in the New York Times, and then sort of questioned again by the New York Times.
But the thing that strikes me the most is a quote from former NSA Head Michael Hayden who is on record as saying:
Some vulnerabilities are such that they marginally (but importantly) weaken a system but exploitation still depended on skills, systems and technologies that few, if any, can match. If the judgment is what is called NOBUS (nobody but us could do this), the risk management decision is pretty easy. Of course, that judgment could change over time and still requires continuous due diligence. (Security Current)
Given the ramifications that Heartbleed could potentially have on the fundamental infrastructure of the Internet, if the NSA was involved I think there needs to be some holding of account.

Categories: Internet, Privacy, Security, Technology
Reported fairly widely in the press is the story about a 5 year old managing to gain access to his father’s X Box Live account and access otherwise restricted video games.
The reports seem very consistent detailing the steps he went through to gain access to the account. Essentially finding a vulnerability in the password reset feature of the X Box One log on screen.
Microsoft have apparently rewarded the youngster with money, games and recognition; and for a 5 year old it must be a nice little 15 minutes of fame, not to mention free games.
What I am a little concerned about is that with all this coverage, no one seems to be asking how a vulnerability that is simple enough for a 5 year old to discover and exploit managed to get into a production system. Also, where else is the code for authentication used?
Don’t get me wrong, I am all for supporting innovation in security research at any age. But let’s get some perspective and start asking the questions that should really be asked.
For details either Google it, or try this link:
http://www.tomshardware.com/news/microsoft-xbox-one-security-5-year-old,26471.html

A lot is said these days of citizen journalism and the rise of social media replacing old media institutions that don’t move with the times. While this year has seen a groundswell of change in the Middle East, in part assisted by these new Internet based methods of organisation and information dissemination, let us not forget the need that still exists for the profession of journalism and the impact of the failure this profession has had on society in the last decade.
The main case in evidence that I refer to is the case made for the regime change in Iraq. Certainly no one can rationally state that there was not evil and corruption present within that country and that something needed to be done. However, the reasons that were given for the action taken in 2003 and the lack of detailed analysis and coverage did not do honour to the individuals involved who sacrificed so much.
But this has happened and much has been claimed, discussed, refuted and the like over the rights and wrongs of the event. Little could be said in this posting that hasn’t already been covered in far greater detail elsewhere.
The one thing that does concern me that seems to have had little to no coverage is the fact little has changed with the media and journalistic institutions since then. The example that illustrates this is the lack of coverage given to an article in the UK Guardian of an interview with Rafid Ahmed Alwan al-Janabi. Codenamed “Curveball”, Rafid Ahmed Alwan al-Janabi provided evidence ultimately used by Colin Powell in his speech to the UN on the case for war with Iraq. The recent article in the Guardian is an interview in which Rafid Ahmed Alwan al-Janabi admits that these were lies told with the purpose of helping to prompt the action that we saw taken in 2003.
Why is this not receiving more coverage? It could be easily argued that the ramifications of this lie has had impact (both negative and positive) to thousands of lives across many countries. Doesn’t it deserve a few more “column inches” that what we are seeing? Shouldn’t the media organisations who in 2002 blindly accepted the corporate line have the courage to admit their errors and pledge in future to do their jobs in helping to maintain a free and truthful press?
A transparent and accurate media is one of the most important tools in maintaining freedom. Let’s not let it disappear

An article posted in The Economist a few years ago presents an interesting take on the safety messages you hear every time you fly in a commercial airline.
GOOD morning, ladies and gentlemen. We are delighted to welcome you aboard Veritas Airways, the airline that tells it like it is. Please ensure that your seat belt is fastened, your seat back is upright and your tray-table is stowed. At Veritas Airways, your safety is our first priority. Actually, that is not quite true: if it were, our seats would be rear-facing, like those in military aircraft, since they are safer in the event of an emergency landing. But then hardly anybody would buy our tickets and we would go bust.
The flight attendants are now pointing out the emergency exits. This is the part of the announcement that you might want to pay attention to. So stop your sudoku for a minute and listen: knowing in advance where the exits are makes a dramatic difference to your chances of survival if we have to evacuate the aircraft. Also, please keep your seat belt fastened when seated, even if the seat-belt light is not illuminated. This is to protect you from the risk of clear-air turbulence, a rare but extremely nasty form
of disturbance that can cause severe injury. Imagine the heavy food trolleys jumping into the air and bashing into the overhead lockers, and you will have some idea of how nasty it can be. We don’t want to scare you. Still, keep that seat belt fastened all the same.Your life-jacket can be found under your seat, but please do not remove it now. In fact, do not bother to look for it at all. In the event of a landing on water, an unprecedented miracle will have occurred, because in the history of aviation the number of wide-bodied aircraft that have made successful landings on water is zero. This aircraft is equipped with inflatable slides that detach to form life rafts, not that it makes any difference. Please remove high-heeled shoes before using the slides. We might as well add that space helmets and anti-gravity belts should also be removed, since even to mention the use of the slides as rafts is to enter the realm of science fiction.
Please switch off all mobile phones, since they can interfere with the aircraft’s navigation systems. At least, that’s what you’ve always been told. The real reason to switch them off is because they interfere with mobile networks on the ground, but somehow that doesn’t sound quite so good. On most flights a few mobile phones are left on by mistake, so if they were really dangerous we would not allow them on board at all, if you think about it. We will have to come clean about this next year, when we introduce in-flight calling across the Veritas fleet. At that point the prospect of taking a cut of the sky-high calling charges will miraculously cause our safety concerns about mobile phones to evaporate.
On channel 11 of our in-flight entertainment system you will find a video consisting of abstract imagery and a new-age soundtrack, with a voice-over explaining some exercises you can do to reduce the risk of deep-vein thrombosis. We are aware that this video is tedious, but it is not meant to be fun. It is meant to limit our liability in the event of lawsuits.
Once we have reached cruising altitude you will be offered a light meal and a choice of beverages (a word that sounds so much better than just saying drinks, don’t you think?)Â The purpose of these refreshments is partly to keep you in your seats where you cannot do yourselves or anyone else any harm. Please consume alcohol in moderate quantities so that you become mildly sedated but not rowdy. That said, we can always turn the cabin air-quality down a notch or two to help ensure that you are sufficiently drowsy.
After take-off, the most dangerous part of the flight, the captain will say a few words that will either be so quiet that you will not be able to hear them, or so loud that they could wake the dead. So please sit back, relax and enjoy the flight. We appreciate that you have a choice of airlines and we thank you for choosing Veritas, a member of an incomprehensible alliance of obscure foreign outfits, most of which you have never heard of. Cabin crew, please make sure we have remembered to close the doors. Sorry, I mean doors to automatic and cross-check. Thank you for flying Veritas.
Enjoy your next flight!

Granted part #1 of this article turned out to be a little more complex to execute that first reported (don’t believe EVERYTHING you read in a blog!), but this one turns out to be a little more serious.
Reported fairly widely in the mainstream tech-press, this vulnerability permits the retrieval of private data from the iPhone and bypasses any user passcode available. Looking at the process involved, this puts the technique into the hand of someone with mid-level technical expertise (thankfully we aren’t quite at the Hollywood-security model of hitting a few keystrokes to bypass a password prompt).
The following video gives you a good demonstration of the process and for those wanting a little more detail, the technical paper supporting this process can be found here.

Categories: General Tech, Security, Technology
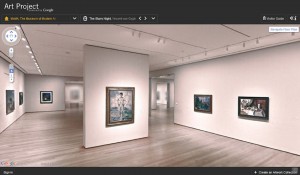
Launched recently with next to no publicity is Google’s interesting new application of the technology perfected with Google Street View call the Google Art Project (http://www.googleartproject.com/).
Instead of driving down your street taking photographs, Google have removed the Street View rig off the van (hopefully!) and gone into a number of world renowned art galleries.
The concepts is the same as Street View, only applied to the gallery and the art displayed within. The site will give you the opportunity to take a tour around the selected art gallery in the same way you could tour around a select street.
As I said, this has been fairly under reported in general and the news that you can find on the site seems to be a little picky about the implementation and the concept in general (see Google Art Project is underwhelming, Google Art Project is second rate and Is the Google Art Project the best thing since real eyes: Critics respond). Also let’s not forget that in this day and age there is little that is genuinely new; Synethescape have also come up with a similar and very functional concept themselves.
But when all is said and done, I think there are two things that should be noted about this project. Firstly, art should be for everyone and not just those in close proximity to it. This isn’t a replacement for a trip to an art gallery by any means, but makes far away galleries and artwork more accessible to anyone with a computer or a local Internet cafe. Also, like most Google project I would expect that this takes a similar “beta” approach. Try it out, throw it to the public and see what works. It has served them well so far (minus a few exceptions…. Wave does come to mind!)
Secondly, and I think more importantly this demonstrates a potentially lucrative commercialisation of the Street View technology. Taking the camera off the street and into a building can provide a number of opportunities for business of all kinds. Imagine being able to virtually enter the world’s biggest and most famous stores from the comfort of your own keyboard. Being able to buy “off the rack” from Harrods or London, or Bloomingdale’s of New York. Being able to click on a store item and then be redirected to an online shopping portal to purchase the product that you just virtually selected.
I don’t think we are there yet, but I do believe it presents and interesting amount of scope for the future of the online shopping experience. As altruistic as the Art Project may be, remember Google likes making money too!

Categories: Google, Internet, Technology
Home Internet with Anonymity Built In
With the debate about online privacy, anti-tracking, clean filter and the like raging and will no doubt to be raised again this year, this is a project that may gain some traction.
For the technically inclined, there are any number of products that will provide this type of function. However, for the less than technically inclined having the configuration built into the router itself may prove to be a more comfortable option.

Categories: Censorship, Internet, Internet Filter, Privacy
For those of you who think that censorship hasn’t yet hit the Internet….read on:
Google Instant is the latest incarnation of the search engine that fills in potential responses as you type them into the Google search bar. Some people think this is great while others feel like Google is reading their minds and are freaked out by it. We believe it’s fun for at least one reason.
Like everything these days, great care must be taken to ensure that as few people as possible are offended by anything. Google Instant is no exception. Somewhere within Google there exists a master list of “bad words” and evil concepts that Google Instant is programmed to not act upon, lest someone see something offensive in the instant results… even if that’s exactly what they typed into the search bar. We call it Google Blacklist.
Give it a try. Go to the Google home page. Type in “puppy” and see the many results that fill your screen. Now type “bitch” and admire the blank screen. In this case, the two words could mean the exact same thing. But Google Instant is erring on the side of caution, protecting the searcher from seeing something they may not want to see.
Obviously, all you have to do is hit return to get the results like you always could. However, even when your request isn’t blacklisted, you’re not getting the SAME results that you would get by hitting return. Entering “murder” into the search bar and hitting a space gets you suggestions of mostly band names. It’s only after you hit return that you can learn the other sinister meaning of the word. What we have here is a demonstration of how content can be filtered, controlled, and ultimately suppressed. It is indeed a good thing that Google isn’t evil.
If you would like to see the words that 2600 have confirmed already to be on the “blacklist”, check this link

 Previous Entries
Previous Entries