There has been some growing speculation as to whether the NSA was aware of the Heartbleed vulnerability in advance. The story was raised and reported by Bloomberg, denied in the New York Times, and then sort of questioned again by the New York Times.
But the thing that strikes me the most is a quote from former NSA Head Michael Hayden who is on record as saying:
Some vulnerabilities are such that they marginally (but importantly) weaken a system but exploitation still depended on skills, systems and technologies that few, if any, can match. If the judgment is what is called NOBUS (nobody but us could do this), the risk management decision is pretty easy. Of course, that judgment could change over time and still requires continuous due diligence. (Security Current)
Given the ramifications that Heartbleed could potentially have on the fundamental infrastructure of the Internet, if the NSA was involved I think there needs to be some holding of account.

Categories: Internet, Privacy, Security, Technology
Reported fairly widely in the press is the story about a 5 year old managing to gain access to his father’s X Box Live account and access otherwise restricted video games.
The reports seem very consistent detailing the steps he went through to gain access to the account. Essentially finding a vulnerability in the password reset feature of the X Box One log on screen.
Microsoft have apparently rewarded the youngster with money, games and recognition; and for a 5 year old it must be a nice little 15 minutes of fame, not to mention free games.
What I am a little concerned about is that with all this coverage, no one seems to be asking how a vulnerability that is simple enough for a 5 year old to discover and exploit managed to get into a production system. Also, where else is the code for authentication used?
Don’t get me wrong, I am all for supporting innovation in security research at any age. But let’s get some perspective and start asking the questions that should really be asked.
For details either Google it, or try this link:
http://www.tomshardware.com/news/microsoft-xbox-one-security-5-year-old,26471.html

Granted part #1 of this article turned out to be a little more complex to execute that first reported (don’t believe EVERYTHING you read in a blog!), but this one turns out to be a little more serious.
Reported fairly widely in the mainstream tech-press, this vulnerability permits the retrieval of private data from the iPhone and bypasses any user passcode available. Looking at the process involved, this puts the technique into the hand of someone with mid-level technical expertise (thankfully we aren’t quite at the Hollywood-security model of hitting a few keystrokes to bypass a password prompt).
The following video gives you a good demonstration of the process and for those wanting a little more detail, the technical paper supporting this process can be found here.

Categories: General Tech, Security, Technology
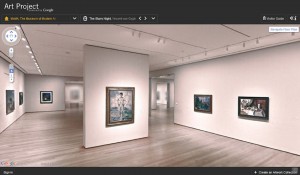
Launched recently with next to no publicity is Google’s interesting new application of the technology perfected with Google Street View call the Google Art Project (http://www.googleartproject.com/).
Instead of driving down your street taking photographs, Google have removed the Street View rig off the van (hopefully!) and gone into a number of world renowned art galleries.
The concepts is the same as Street View, only applied to the gallery and the art displayed within. The site will give you the opportunity to take a tour around the selected art gallery in the same way you could tour around a select street.
As I said, this has been fairly under reported in general and the news that you can find on the site seems to be a little picky about the implementation and the concept in general (see Google Art Project is underwhelming, Google Art Project is second rate and Is the Google Art Project the best thing since real eyes: Critics respond). Also let’s not forget that in this day and age there is little that is genuinely new; Synethescape have also come up with a similar and very functional concept themselves.
But when all is said and done, I think there are two things that should be noted about this project. Firstly, art should be for everyone and not just those in close proximity to it. This isn’t a replacement for a trip to an art gallery by any means, but makes far away galleries and artwork more accessible to anyone with a computer or a local Internet cafe. Also, like most Google project I would expect that this takes a similar “beta” approach. Try it out, throw it to the public and see what works. It has served them well so far (minus a few exceptions…. Wave does come to mind!)
Secondly, and I think more importantly this demonstrates a potentially lucrative commercialisation of the Street View technology. Taking the camera off the street and into a building can provide a number of opportunities for business of all kinds. Imagine being able to virtually enter the world’s biggest and most famous stores from the comfort of your own keyboard. Being able to buy “off the rack” from Harrods or London, or Bloomingdale’s of New York. Being able to click on a store item and then be redirected to an online shopping portal to purchase the product that you just virtually selected.
I don’t think we are there yet, but I do believe it presents and interesting amount of scope for the future of the online shopping experience. As altruistic as the Art Project may be, remember Google likes making money too!

Categories: Google, Internet, Technology
Home Internet with Anonymity Built In
With the debate about online privacy, anti-tracking, clean filter and the like raging and will no doubt to be raised again this year, this is a project that may gain some traction.
For the technically inclined, there are any number of products that will provide this type of function. However, for the less than technically inclined having the configuration built into the router itself may prove to be a more comfortable option.

Categories: Censorship, Internet, Internet Filter, Privacy
For those of you who think that censorship hasn’t yet hit the Internet….read on:
Google Instant is the latest incarnation of the search engine that fills in potential responses as you type them into the Google search bar. Some people think this is great while others feel like Google is reading their minds and are freaked out by it. We believe it’s fun for at least one reason.
Like everything these days, great care must be taken to ensure that as few people as possible are offended by anything. Google Instant is no exception. Somewhere within Google there exists a master list of “bad words” and evil concepts that Google Instant is programmed to not act upon, lest someone see something offensive in the instant results… even if that’s exactly what they typed into the search bar. We call it Google Blacklist.
Give it a try. Go to the Google home page. Type in “puppy” and see the many results that fill your screen. Now type “bitch” and admire the blank screen. In this case, the two words could mean the exact same thing. But Google Instant is erring on the side of caution, protecting the searcher from seeing something they may not want to see.
Obviously, all you have to do is hit return to get the results like you always could. However, even when your request isn’t blacklisted, you’re not getting the SAME results that you would get by hitting return. Entering “murder” into the search bar and hitting a space gets you suggestions of mostly band names. It’s only after you hit return that you can learn the other sinister meaning of the word. What we have here is a demonstration of how content can be filtered, controlled, and ultimately suppressed. It is indeed a good thing that Google isn’t evil.
If you would like to see the words that 2600 have confirmed already to be on the “blacklist”, check this link

At first glance this could be some talented computer animators take on Google. However, when you add the fact that it was a paid commercial shown in Times Sqaure on the Jumbotron it takes on a bit of a new meaning.
Essentially this is a fight between a privacy advocate group and Google (who appear to have snubbed them at their own peril) over liberties taken with the use of user (i.e. most of the Internet) personal information.
While I think their intentions may be noble, I think they are fighting a battle that has been fought, lost and celebrated by the victor over a few generations! If you wanted privacy on the Internet, around 1995 was the time to put these mechanisms in place.
Two refuges exist for the true privacy seeker:
- Stay offline
- Get to know Tor, BetterPrivacy for FireFox and PGP
(Oh, and slight irony alert. I wonder how much YouTube found out about you and your viewing preferences while watching this video?)

Categories: Internet, Privacy, Security, Social Comment, Technology, Video
Someone in the US Cyber Command HQ at Ft Meade has a slight sense of humour. Check out their logo
Can you spot the hidden message (hint….you may need to click on the image to enlarge it)?
I will reveal it only because anyone with the ability to Google will no doubt be able to get the answer. Look at the text around the inner circle of the logo. You will see the following numbers and letters:
9ec4c12949a4f31474f299058ce2b22a
What does it all mean? Try running the string through a md5 decoding utility like the one located here and see what you get.
Listen…….can you hear the sound of Dan Brown working on his new novel as we speak?

Categories: Internet, Technology
It would seem that Apple have now gone into damage control with the Antennagate problem touched upon in the last New Tech Order post. It appears that Apple have announced that they will be providing free bumper cases to disgruntled iPhone 4 owners or providing refunds for those who have already purchased one.
Too little too late? Hard to say at this point, at least it seems that Apple PR are starting along the right track. However, will this be the advantage need for those nipping at Apples heels to take?
And on the topic of Apple troubles, it would seem that my upgrade to iOS 4.0 and the subsequent 4.0.1 seems to have been a lucky one. Widespread reports are filtering through of massive performance issues post upgrades for iPhone 3G and 3GS users! Lucky me…I guess.

Apple have made their iOS 4.0.1 software upgrade available today. Unlike other upgrades, you don’t receive a critical security fix that will keep you safer, and you don’t get a new feature that will make your use of the phone even more complete. What you do get is a better way of displaying how well (or how bad) the phone reception is in your area.
This is in response to the recent bad press received by the launch of the new iPhone 4 regarding the loss of signal that can occur when you are holding the phone. Apple admitted that the algorithm to calculate the number of bars shown for a given signal strength was incorrect and this new and complete iOS update will fix that “problem”.
This is truly a great and worthy update to spend time downloading. You will now see just exactly how crap the phone service in your area actually is instead of being lulled into a false sense of security with the full 5 bars at all times until you are out of range.
While I think the iPhone 4 is a nice piece of design work and will no doubt raise the bar yet again amongst handset makers to try and compete, it does highlight one major design flaw that seems evident across a range of technology devices; design over function.
Devices that are designed to send and receive signals require an antenna. Very simple, something that has been known about radio based transmission devices for a large number of years now. Unfortunately the antenna on the common mobile phone seems to have gradually over time vanished. The average consumer possible thought that new technology came about to relieve the need for an antenna, however not really. All phones regardless of model or design have an antenna place somewhere within the device. It may not be obvious however it is there.
In the case of the iPhone 4, it would seem that the need to keep to the design standard of Apple won out over the need to actually produce a product that would viably work in common use scenarios. The antenna on the iPhone 4 is actually wrapped around the outside of the casing in an effort to save space. Holding the phone (as you normally would while making a phone call) attenuates the signal to the point where it may either lose the call or connection you are on or at the very least degrade it.
Now comes the corporate spin part. One possible fix to this problem is to use the Apple produced iPhone 4 bumper case. Hmmm, could it be possible that Apple were prepared for this occurrence?


 Previous Entries
Previous Entries